Challenge 2:Case Of Client Side Code (Part 1)
This is a detailed writeup created for challenges associated with the Certified Web AppSecurity Expert (CWAE) certification.
Challenge/Task
- Stored Cross-Site Scripting (XSS)
- DOM-Based Cross-Site Scripting (XSS)
1. First XSS - Stored Cross-Site Scripting (XSS)
Proof-of-Concept (POC):
From previous challenge, we have found a website which is https://the-abstractors.com/. After further checking, there is a signup page that everyone can register as a user.
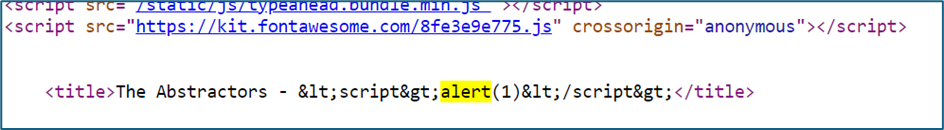
As a tester, we will play around all the functions/button/form inside the website. There is a page where we can write a post. I try to inject xss script inside all the field. In the Title field, the payload can’t be executed because the <> tag is been encoded 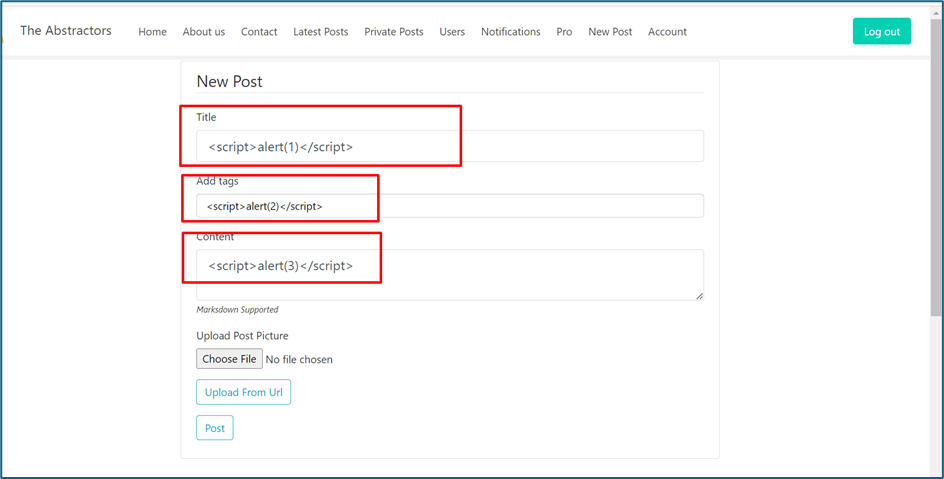
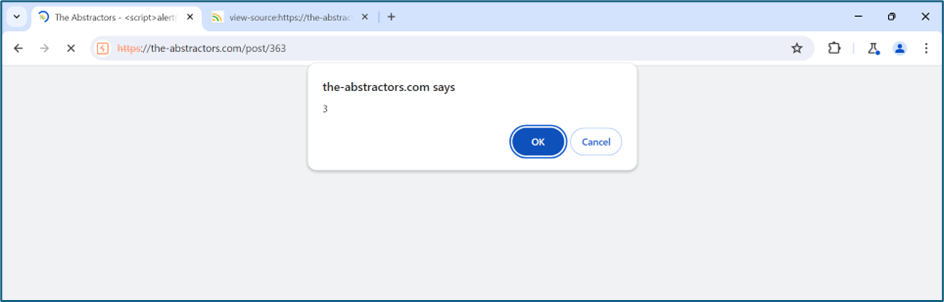
However, in content, seems we can execute the payload but the alert is not pop-up. 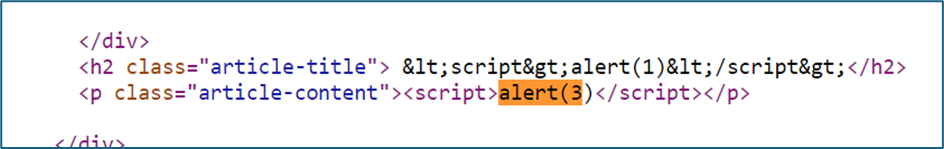
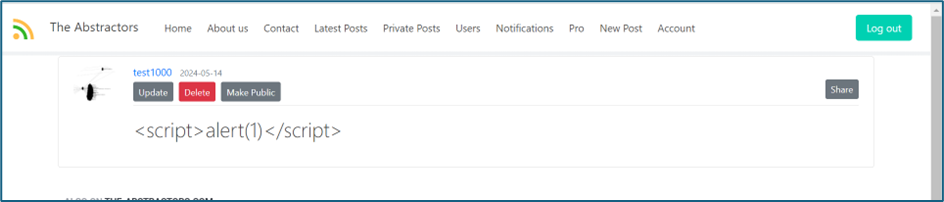
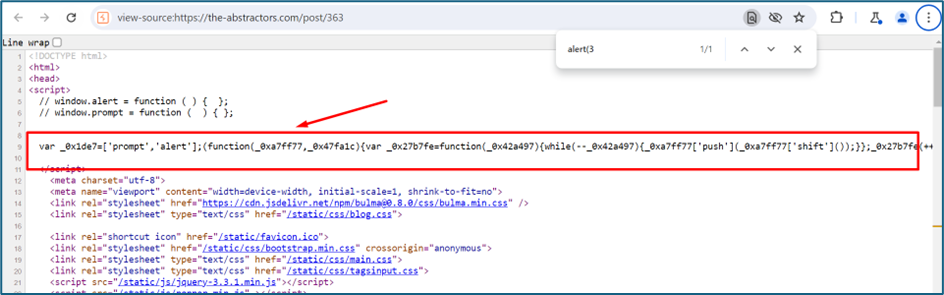
Upon checking the source code, there is a line to avoid the system from execute the alert and prompt function.
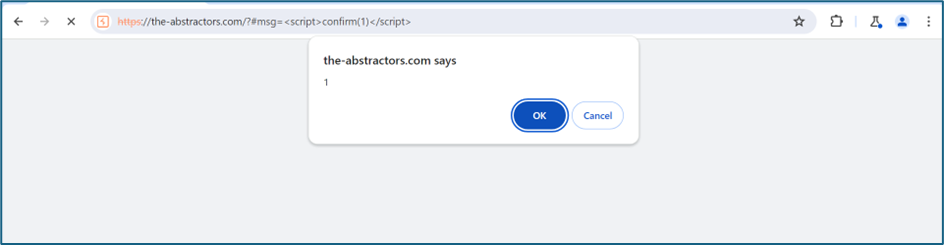
We try to use other function which is confirm function. 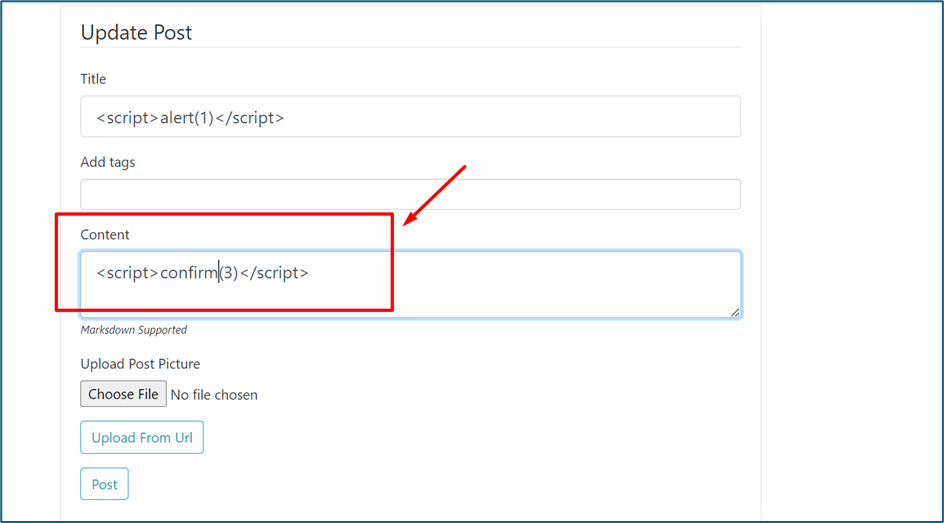
XSS found using confirm function.
2. Second XSS – DOM Based XSS
Upon checking the chat function, my message is not sent to the server. 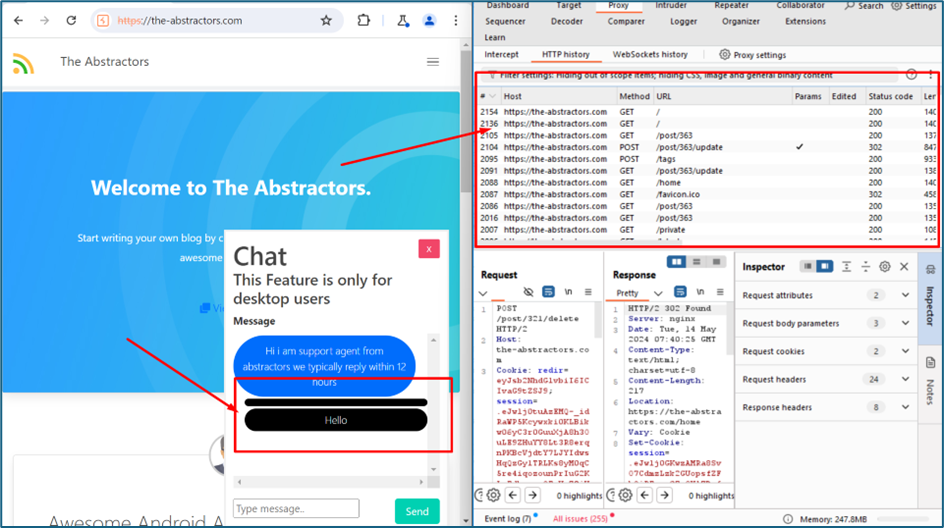
Looking at the source code, it just a DOM function. 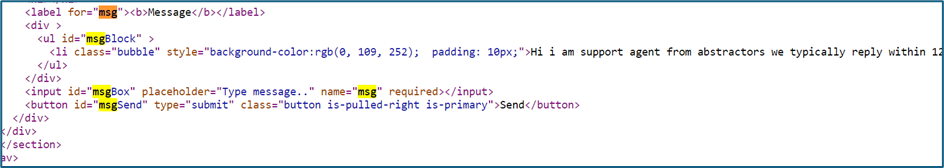
Send the XSS payload and it popup the confirm (). 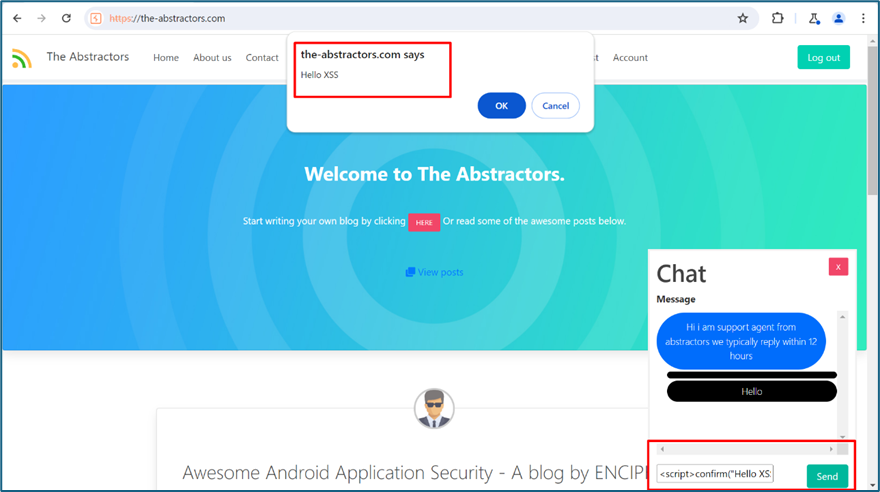
So from the vulnerabilities, I can craft a link that contains xss payload and send it to everyone.