Challenge 4:GhostScript Infiltration
This is a detailed writeup created for challenges associated with the Certified Web AppSecurity Expert (CWAE) certification.
Challenge/Task
- Out of The Box
Proof-of-Concept (POC):
There are multiple places in this system have an upload function. For example in this page, we can upload our profile image.
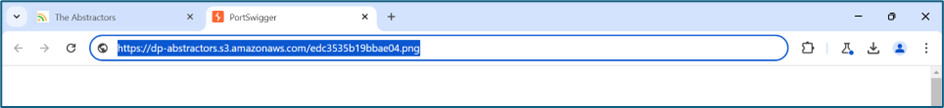
https://dp-abstractors.s3.amazonaws.com/edc3535b19bbae04.png Upon checking the address, it is an S3 bucket hosting all the profile images of the users. 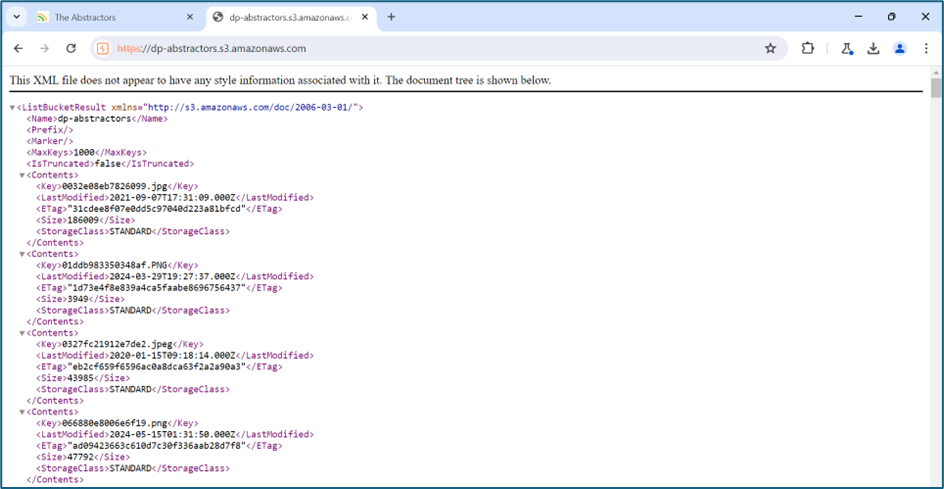
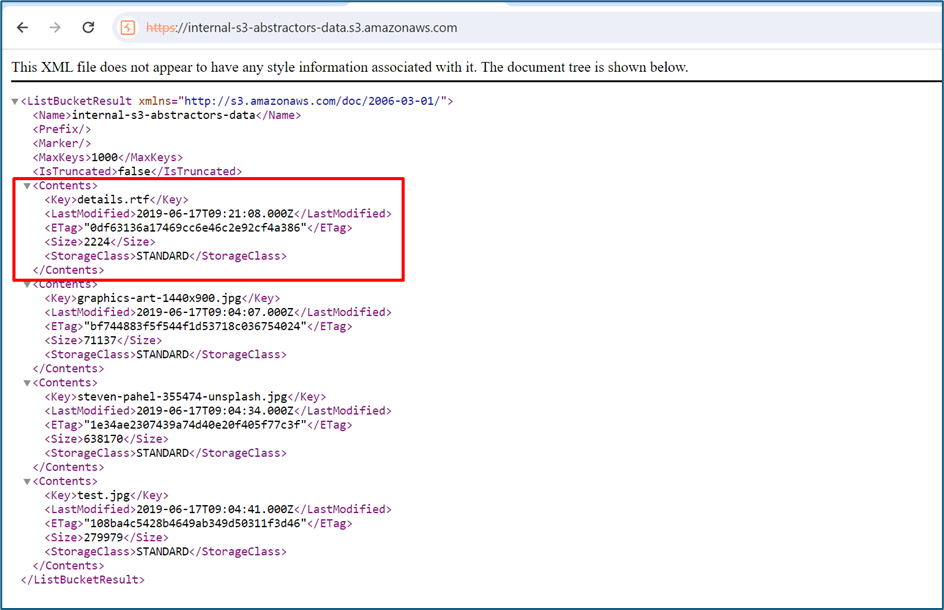
Previously in another challenge we already performed a subdomain scanning. I found out there is a subdomain which refers to the S3 which is s3.the-abstractors.com. Upon digging, the cname record is referring to internal-s3-abstractors-data.s3.amazonaws.com 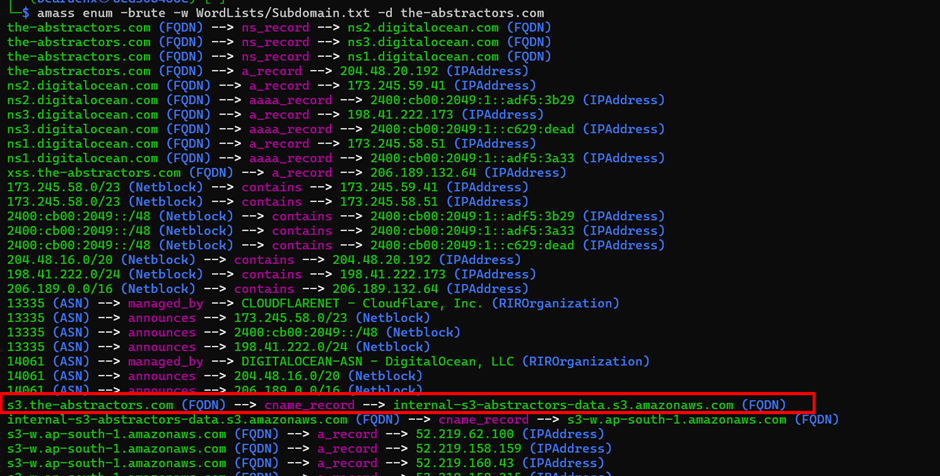
I visited the domain and found out few interesting files including details.rtf.
I visited the domain and found out few interesting files including details.rtf. 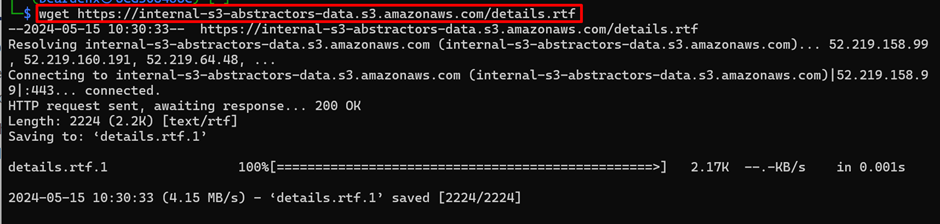
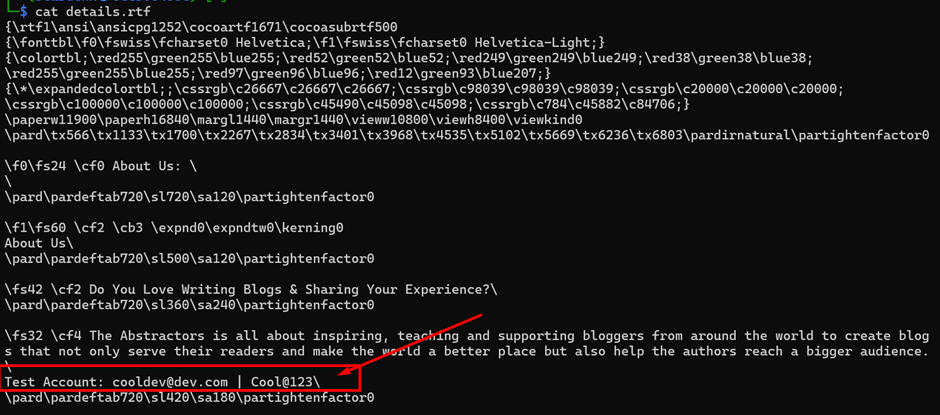
Using cat command, I read the file and found an interesting credential which may belongs to dev team,
I use the credential and try to login to the system using the credential.